Cloud Computing
Top News
- Google to End Email Content Scanning: After a decade of controversy, Google announced that it will stop scanning the content of all Gmail. Google stopped scanning e-mails for education in 2014 after a lawsuit charged that it violated wiretap laws. Google faced similar allegations in many other cases in the United States and around the world. EPIC warned about Google's e-mail scanning practices back in 2005 and filed a complaint with the FTC in 2009 over the privacy risks in Google's insecure cloud computing services, including Gmail. In 2014, EPIC led a successful campaign to stop Google from scanning student emails for commercial advertising. Last year, EPIC filed a friend-of-the-court brief in a Massachusetts case, again objecting to Google's Gmail scanning. EPIC explained in 2005 that Google's email service undermined online privacy and prevented the adoption of important security methods, such as end-to-end encryption. (Jun. 23, 2017)
- Google Transparency Report Reveals Risks of Cloud-based Computing: According to a recent report from Google, the company received 20,938 requests for user data in the first half of 2012, up from 18,257 requests in the second half of 2011. The United States accounted for 7,969 requests in the 2012 report. And of these requests, Google provided user data to the US government in 90% of the cases. Over the last several years, Google has pursued an aggressive effort to promote computing services that store personal data on Google's servers even as the number of government requests has grown. And earlier this year, Google reduced safeguards for Gmail users, over the objections of many lawmakers and users, when it consolidated privacy policies across its various Internet services. In 2009, EPIC L3[urged] the Federal Trade Commission to look more closely at the privacy risks of cloud-based services. For more, see EPIC - "Cloud Computing". (Nov. 14, 2012)
- European Expert Group Affirms Privacy Rules for Cloud Service Providers (Jul. 3, 2012) +
- Google Terms of Service Grant Company Broad Rights over Data of Google Drive Users (Apr. 26, 2012) +
- Google Backs Off Privacy Policy Change for Federal Government (Feb. 3, 2012) +
- Twitter Adopts Privacy Enhancing Technique, Defaults to HTTPS (Aug. 24, 2011) +
- Chairman Leahy Announces New Subcommittee on Privacy and Technology (Feb. 16, 2011) +
- Facebook Enables Full-Session Encryption (Feb. 7, 2011) +
- NIST Seeks Comments on Guidelines for Cloud Computing (Feb. 3, 2011) +
- DHS Privacy Office Releases 2010 Annual Report (Sep. 24, 2010) +
- Google Adds Two-Factor Authentication to Google Apps (Sep. 24, 2010) +
- Pew/Elon Study: Cloud Computing Will Expand, Security and Privacy Issues Must be Addressed (Jun. 11, 2010) +
- Congress Pursues Investigation of Google and Facebook's Business Practices (Jun. 1, 2010) +
- Congress Urges FTC to Investigate Google Following Revelation that "Street View" Scarfed Wi-Fi Data (May. 19, 2010) +
- FCC Release National Broadband Plan, Privacy Strategy Unclear (Mar. 17, 2010) +
- EPIC Recommends Effective Consumer Privacy Standards, Calls Notice and Choice a "Failed Experiment" (Mar. 17, 2010) +
- EPIC Seeks Records on Google-NSA Relationship (Feb. 4, 2010) +
- EPIC Urges FTC to Protect Users' Privacy On Cloud Computing and Social Networking Services (Jan. 28, 2010) +
- FTC Tells FCC it is Pursuing EPIC's Cloud Computing Complaint (Jan. 6, 2010) +
- ENISA Report Examines Cloud Computing and Privacy (Nov. 25, 2009) +
- Administration Announces Cloud Computing Initiative, but Privacy Umbrella Missing (Sep. 17, 2009) +
- EPIC Forces Disclosure of Government Contracts with Social Media Companies, Privacy Terms Missing (Aug. 12, 2009) +
- Expert Group Asks Google to Improve Cloud Computing Privacy (Jun. 16, 2009) +
- EPIC Urges Privacy Protections for Government's Use of Social Media (Jun. 3, 2009) +
- EPIC Seeks Government Agreements with Social Networking Companies (Apr. 30, 2009) +
- Federal Trade Commission to Review EPIC Cloud Computing Complaint (Mar. 19, 2009) +
- EPIC Petitions FTC to Investigate Google, Cloud Computing Services (Mar. 17, 2009) +
More top news
What is Cloud Computing?
Cloud computing refers to data, processing power, or software stored on remote servers made accessible by the Internet as opposed to one's own computers. The term "the cloud" comes from computer network diagrams which, because the individual computers that formed its components were too numerous to show individually, depicted the Internet as a vast cloud at the top of the network chain. One of the key features of cloud computing is that the end users does not own the technology they are using. All the hardware and software is owned by a cloud computing service, while the user simply rents time or space. Several cloud computing applications, such web email, wiki applications, and online tax preparation, have become common experiences for the average Internet user.
For users, cloud computing arrangements can bring about major cost reductions and efficiencies. For example, in a cloud computing arrangement the end user does not have to pay large up front capital costs for hardware or for that hardware's continued maintenance. If the user needs temporary additional space, he can simply tell the cloud service provider to up his quota for the time being, rather than purchase additional physical capacity which would only be needed for a short period and then left idle. This also means that computer resources as a whole are generally used more efficiently. Rather than have lots of machines running a few tasks and then wasting the rest of their computing power, cloud computing allows a few machines to do lots of tasks without wasted computing cycles. Cloud Computing can be thought of as a way to make the world of computer resources seamlessly scalable.
At the same time, cloud computing also creates dependency. The emergence of cloud computing services is structured around a re-imagining of the relationship between technology and end users. The end user must rely on the cloud computing service provider to ensure that data is kept secure and reliably accessible. They must also depend on the telecommunications infrastructure that will act as the delivery and retrieval pathways for the flow of data to and from the cloud. The further away users are from the underlying technology that they rely upon, the more dependent the relations may become. In addition, once an end user adopts a cloud computing arrangement it may be difficult to move back to a personal computing based platform for data services.
The move toward computing resources as a service to be provided by remote sources with greater access to unbounded computing power presents some attraction to computer users with limited resources and a growing need for information services, but it also presents serious issues that must be examined.
Background
Although cloud computing has only matured in recent years, the underlying concept of multiple users sharing computer resources is not new. The earliest computing operations allowed multiple users to bring work projects, usually in the form of data encoded onto punch cards, magnetic tapes, or floppy disks to a central stand-alone computer for processing. These stand-alone computers could only perform one job or task at a time, and, as a result, they were kept frequently in use processing one user's task after the next.
In 1969, the Department of Defense's Advance Research Projects Agency sought to expand the distances over which computers could reliably communicate. At the time the project was undertaken, the cost of a computer was very high and processing speed was much slower than today's computing systems. Often times a computers could be tied up for hours, days, or even weeks on a single project. The ARPAnet project sought to create a platform that would allow distributed users to share their valuable computing resources and collaborate on documents. Using the ARPAnet, a user could access a computer located elsewhere on the network and function as a local user at the remote site. The ARPAnet mainly linked government agencies and universities, but it was out of the ARPAnet that what we now know as the Internet was originally developed.
With the development of the operating system, stand-alone computers could perform multiple functions simultaneously for the first time. This opened the door for the first instances of multiple users using a system at the same time. Early instances of multiple clients sharing a single, sometimes more powerful, computing device were known as local area networks. In these settings, a single central server or computing device supported several stand-alone personal computers or dumb terminals (keyboards and computer screens) housed in the same physical location. The terminals would connect to the central server, which would do the terminal's actual processing.
Cloud Computing is an evolution from these previous efforts at shared computing. As prices for processing power and storage have fallen and high-speed internet connections have become ubiquitous, cloud computing has become an increasingly attractive option for many individuals and businesses. As of September 2008, 69 percent of Americans were using webmail services, storing data online, or otherwise using software programs, such as word processing applications, whose functionality is located on the web.
Types of Cloud Computing Services
There are three basic types of cloud computing:
1. Software as a Service (SaaS) is the most common and widely known type of cloud computing. SaaS applications provide the function of software that would normally have been installed and run on the user's desktop. With SaaS, however, the application is stored on the cloud computing service provider's servers and run through the user's web browser over the Internet. Examples of SaaS include: Gmail, Google Apps, and Salesforce.
2. Platform as a Service (PaaS) cloud computing provides a place for developers to develop and publish new web applications stored on the servers of the PaaS provider. Customers use the Internet to access the platform and create applications using the PaaS provider's API, web portal, or gateway software. Examples of PaaS include: Saleforce's Force.com, Google App Engine, Mozilla Bespin, Zoho Creator.
3. Infrastructure as a Service (IaaS) seeks to obviate the need for customers to have their own data centers. IaaS providers sell customers access to web storage space, servers, and Internet connections. The IaaS provider owns and maintains the hardware and customers rent space according to their current needs. An example of Iaas is Amazon Web Services. IaaS is also known as utility computing.
Issues
When users place their data and applications on centralized servers, they lose the ability to maintain complete control of that information. With the rise of cloud computing, critical and sometimes sensitive information that was once safely stored on personal computers now resides on the servers of online companies. Examples of such information including users email, banking information, and full backups of individuals' hard drives. This phenomenon creates a multitude of risks for the users.
One of the biggest risks of storing data in the cloud is the possibility that this data will be accessed by unwanted third parties. While some cloud computing services encrypt user data when it is stored, others store data in clear text, leaving it especially vulnerable to a security breach. Data stored in the cloud might also be provided to marketers. For example, many email providers allow secondary advertising uses for e-mail communications. In recent studies, an overwhelming majority of Cloud Computing Services users expressed serious concern regarding the possibility that a Cloud Computing Services provider would disclose their data to others. According to a report by the Pew Internet and American Life Project, 90% of cloud application users say they would be very concerned if the company storing their data sold it to a third party. 80% of users say they would be very concerned if companies used their photos or other data in marketing campaigns and 68% say they would be very concerned if companies who provided these services analyzed their information and then displayed ads to them based on their actions.
Legal rights and regulatory authority for the protection of the privacy of cloud computing users are not well defined. Data stored in the cloud may be subject to less stringent legal protection than data stored on a personal computer. Under the Electronic Communications Privacy Act, data stored in the cloud may be subject to a lesser standard for law enforcement to gain access to it than if the data were stored on a personal computer. Moreover, the terms of service for cloud computing services often make clear that they will preserve and disclose information to law enforcement when served with legal process. Health information services that store user medical information may not be subject to the privacy protections of the Health Insurance Portability Protection Act. Even where it is clear that user data is protected, cloud computer service providers often limit their liability to the user as a condition of providing the service, leaving users with limited recourse should their data be exposed or lost.
Storing data in the cloud means that access to that data is subject to the cloud computing service provider's terms. Often the terms of service allow the cloud computing service provider to terminate the service at any time. On the other hand, depending on the terms of service, deleting an account may not actually remove the stored data from the provider's servers. One might also imagine a data hostage scenario where it is vital that a user gain access to online information, but the data holder refuses that access without first receiving a payment or other compensation. In addition, there are serious concerns about the reliability of cloud computing services. As mentioned earlier, if the cloud computing service goes down or loses data, the users would have little legal recourse.
Case Studies
Amazon Web Services
Amazon Web Services (AWS) offers a range of cloud computing services that allow users to "securely" store and manage a wide range of data types. AWS also incorporates identity, payment, database, messaging, and other services.
Amazon promotes AWS as a reliable cloud computing option, but its service level agreement states that "AWS reserves the right to refuse service, terminate accounts, remove or edit content in its sole discretion."
Further, the AWS terms and conditions' "Disclaimer of Warranties and Limitations of Liability," state that:
"AWS DOES NOT WARRANT THAT THIS SITE; INFORMATION, CONTENT, MATERIALS, PRODUCTS (INCLUDING ANY SOFTWARE) OR SERVICES INCLUDED ON OR OTHERWISE MADE AVAILABLE TO YOU THROUGH THIS SITE; ITS SERVERS; OR E-MAIL SENT FROM AWS ARE FREE OF VIRUSES OR OTHER HARMFUL COMPONENTS. AWS WILL NOT BE LIABLE FOR ANY DAMAGES OF ANY KIND ARISING FROM THE USE OF THIS SITE OR FROM ANY INFORMATION, CONTENT, MATERIALS, PRODUCTS (INCLUDING SOFTWARE) OR SERVICES INCLUDED ON OR OTHERWISE MADE AVAILABLE TO YOU THROUGH THIS SITE, INCLUDING, BUT NOT LIMITED TO DIRECT, INDIRECT, INCIDENTAL, PUNITIVE, AND CONSEQUENTIAL DAMAGES, UNLESS OTHERWISE SPECIFIED IN WRITING. CERTAIN STATE LAWS DO NOT ALLOW LIMITATIONS ON IMPLIED WARRANTIES OR THE EXCLUSION OR LIMITATION OF CERTAIN DAMAGES. IF THESE LAWS APPLY TO YOU, SOME OR ALL OF THE ABOVE DISCLAIMERS, EXCLUSIONS, OR LIMITATIONS MAY NOT APPLY TO YOU, AND YOU MIGHT HAVE ADDITIONAL RIGHTS."
As additional protection for itself, Amazon limits all legal actions that may arise over its Cloud Computing services to King County, Washington, where the company is located.
Mozy
Another Cloud Computing service provider Mozy.com offers users cloud computing services to backup photographs, documents, accounting records, or any information that is stored on a personal computer. The service reserves broad rights to "at any time to modify, suspend, or discontinue providing the Service or any part thereof in its sole discretion with or without notice."

The Decho Corporation operates Mozy.com, MozyPro.com and Decho.com. The company considers signing up for the service as an agreement of the terms. The customer may end the agreement by "destroying the Software and closing your account," but it does not address what happens to the information that remains in the hands of the company. Closing an account does not mean that information collected or stored on the service will be removed.

The company defines personal "as any data from which it is practical to directly determine the identity of an individual." Further, under the terms and conditions users are told, "You agree to indemnify, defend, and hold harmless Decho and its suppliers from any and all loss, cost, liability, and expense arising from or related to your data, your use of the Service..."
WebMD
Medical information services, such as WebMD provides tools to users that allow them to establish medical information accounts that can be used to record details regarding health conditions, symptoms, medications, search for medical professionals, and details about the type of medical advice sought.
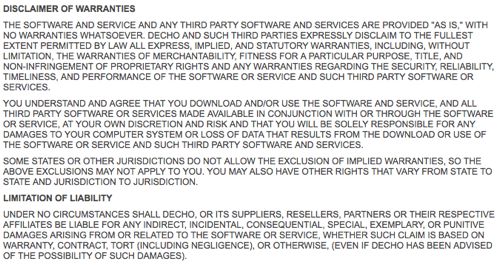
WebMD's Terms and Conditions of Use, state that information provided to them by e-mail, blog posting, uploading photos or video, or submitting information to "Public Areas," this information becomes the property of WebMD.

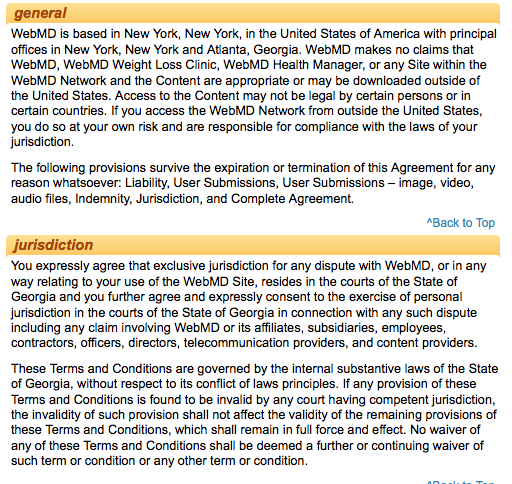
Although federal law allows for patient record privacy though the Health Insurance Portability Protection Act (HIPPA), the records created by WebMD and other health cloud computing services are not covered by HIPPA. WebMD states in its Terms and Conditions of Use that the company will not be liable for any damages.
Resources
- Do You Know Where Your Data is in the Cloud?, Forrester Research.
- EPIC, FTC Complaint Google Cloud Computing Services, March 17, 2009
- Privacy in the Clouds: Risks to Privacy and Confidentiality from Cloud Computing, World Privacy Forum, February, 23, 2009
- An A to Z of Cloud Computing in New York City
- Cloud Computing Workshop, Center for Information Technology Policy, January 14-15, 2008
- Cloud Computing, Wikipedia
- What is Cloud Computing?
- Envisioning the Cloud: The Next Computing Paradigm, Marketplace Report, March 2009
- TCP/IP, Network Administration, Second Edition, Craig Hunt, O'Reilly & Associates, January 1998
- A Brief History of NSF and the Internet
- Architectural manifesto: An introduction to the possibilities (and risks) of cloud computing
Share this page:
Subscribe to the EPIC Alert
The EPIC Alert is a biweekly newsletter highlighting emerging privacy issues.







