Electronic Communications Privacy Act (ECPA)
Top News
- International Privacy Experts Adopt Recommendations for Cross-Border Law Enforcement Requests for Data: The International Working Group on Data Protection in Telecommunications has adopted new recommendations to protect individual rights during criminal cross-border law enforcement. The Berlin-based Working Group includes Data Protection Authorities and experts who assess emerging privacy challenges. The Working Group on Data Protection calls on governments and international organisations to ensure law enforcement requests accord with international human rights norms. The Working Group recommends specific safeguards for data protection and privacy, including accountability, procedural fairness, notice and an opportunity to challenge. EPIC addressed similar issues in an amicus brief for the US Supreme Court in the Microsoft case. EPIC and a coalition of civil society organizations recently urged the Council of Europe to protect human rights in the proposed revision to the Convention on Cybercrime. In April 2017, EPIC hosted the 61st meeting of the IWG in Washington, D.C. at the Goethe-Institut, Germany's cultural institute. (Aug. 14, 2018)
- Amazon Echo Secretly Recorded And Disclosed User's Private Conversation: "Alexa" secretly recorded the private conversation of a Portland woman and sent it to one of her contacts, according to a news report. The Federal Wiretap Act makes it a crime to intentionally intercept a private communication. In 2015, EPIC urged the Federal Trade Commission and the Department of Justice to investigate whether "always on" smart home devices violated federal wiretap law. EPIC recently warned the Consumer Product Safety Commission that the Google Home Mini continuously record users' private conversations because of a product defect. And EPIC recently testified before the CPSC on the need to regulate privacy and security hazards posed by Internet of Things devices. (May. 24, 2018) More top news »
Background
Introduction to ECPA
The Electronic Communications Privacy Act ("ECPA") was passed in 1986 to expand and revise federal wiretapping and electronic eavesdropping provisions. It was enacted to create promote " the privacy expectations of citizens and the legitimate needs of law enforcement." Congress also sought to support the creation of new technologies by assuring consumers that their personal information would remain safe.
ECPA included amendments to the Wiretap Act, created the Stored Communications Act, and created the Pen Register Act. The Wiretap Act concerns interception of electronic and wire communications, which include "any aural transfer made in whole or in part through the use of facilities for the transmission of communications by the aid of wire, cable, or other like connection.” An oral communication is "any oral communication uttered by a person exhibiting an expectation that such communication is not subject to interception under circumstances justifying such expectation"; this constitutes any oral conversation in person where there is the expectation no third party is listening.
Individuals who violate ECPA face up to five years in prison and fines up to $250,000. Victims are also entitled to bring civil suits and recover actual damages, in addition to punitive damages and attorney's fees, for violations. The United States itself cannot be sued under ECPA, but evidence that is gathered illegally cannot be introduced in court.
Prohibition on Interception of Communications
ECPA does include important provisions that protect a person's wire and electronic communications from being intercepted by another private individual. In general, the statute bars wiretapping and electronic eavesdropping, possession of wiretapping or electronic eavesdropping equipment, and the use or disclosure of information unlawfully obtained through wiretapping or electronic eavesdropping. The Wiretap Act prohibits any person from intentionally intercepting or attempting to intercept a wire, oral or electronic communication by using any electronic, mechanical or other device. To be clear, an electronic device must be used to perform the surveillance; mere eavesdropping with the unaided ear is not illegal under ECPA.
There are exceptions to this blanket prohibition, such as if the interception is authorized by statute for law enforcement purposes or consent of at least one of the parties is given. Although some states prohibit the recording of conversations unless all parties consent, ECPA requires only one party consent; an individual can record his own conversation without violating federal law. In the workplace, an employer would likely not violate ECPA by listening to an employee's communications if, for example, blanket consent was given as part of the employee's contract.
In addition to criminalizing the actual wiretapping or electronic eavesdropping, ECPA also prohibits an individual from disclosing such information obtained illegally if the person has reason to know that it was obtained illegally through the interception of a wire, oral, or electronic communication. Similarly, if a person cannot lawfully disclose a lawful law enforcement wiretapping and if he has reason to know that doing so will obstruct a criminal investigation.
Prohibition on Access of Communications
While the Wiretap Act addresses the interception of communications, the Stored Communications Act addresses access to stored communications at rest. In the modern context, this primarily refers to e-mails that are not in transit. The Act makes it unlawful to intentionally access a facility in which electronic communication services are provided and obtain, alter, or prevent unauthorized access to a wire or electronic communication while it is in electronic storage in such system. This statute also makes exceptions for law enforcement access and user consent.
As with other forms of communication protected under ECPA, an employer is generally forbidden from accessing an employee's private e-mails. However, if consent is given in the form of an employment contract that explicitly authorizes the employer to access e-mails, it may be lawful under ECPA for him to do so.
Pen Registers and Trap and Trace
Pen registers and trap and trace devices provide non-content information about the origin and destination of particular communications. Because this information does not contain the content of the communication, it is subject to lesser restrictions than actual content. The Supreme Court has long held that there is no reasonable expectation of privacy in this information because the telecommunications company has ready access to it; in fact, the company must utilize this information to ensure the communications are properly routed and delivered. The Pen-Register Act covers pen registers/trap and trace.
In the context of phone calls, Pen-Registers display the outgoing number and the incoming number. Because e-mail subject lines contain content, their use on e-mails, per revisions in the USA PATRIOT Act, must include the sender and addressee, but avoid any part of the subject. IP addresses and port numbers associated with the communication are also fair game under the Act.
The regulations specifically apply to "devices" that capture this information. Thus, ECPA generally prohibits the installation or use of any device that serves as a pen register or trap and trace. Amendments in the USA PATRIOT Act allow the term devices to also encompass software.
Also, unlike provisions relating to the interception and access of communications, there is no statutory exclusionary rule that applies when the government illegally uses a pen register/trap and trace device. And there is no private cause of action against the government for violations of this law.
Disclosure of Records
ECPA lays out guidelines for law enforcement access to data. Under the Stored Communications Act, the government is able to access many kinds of stored communications without a warrant.
The following table illustrates the different treatment of the contents of an email at various times:
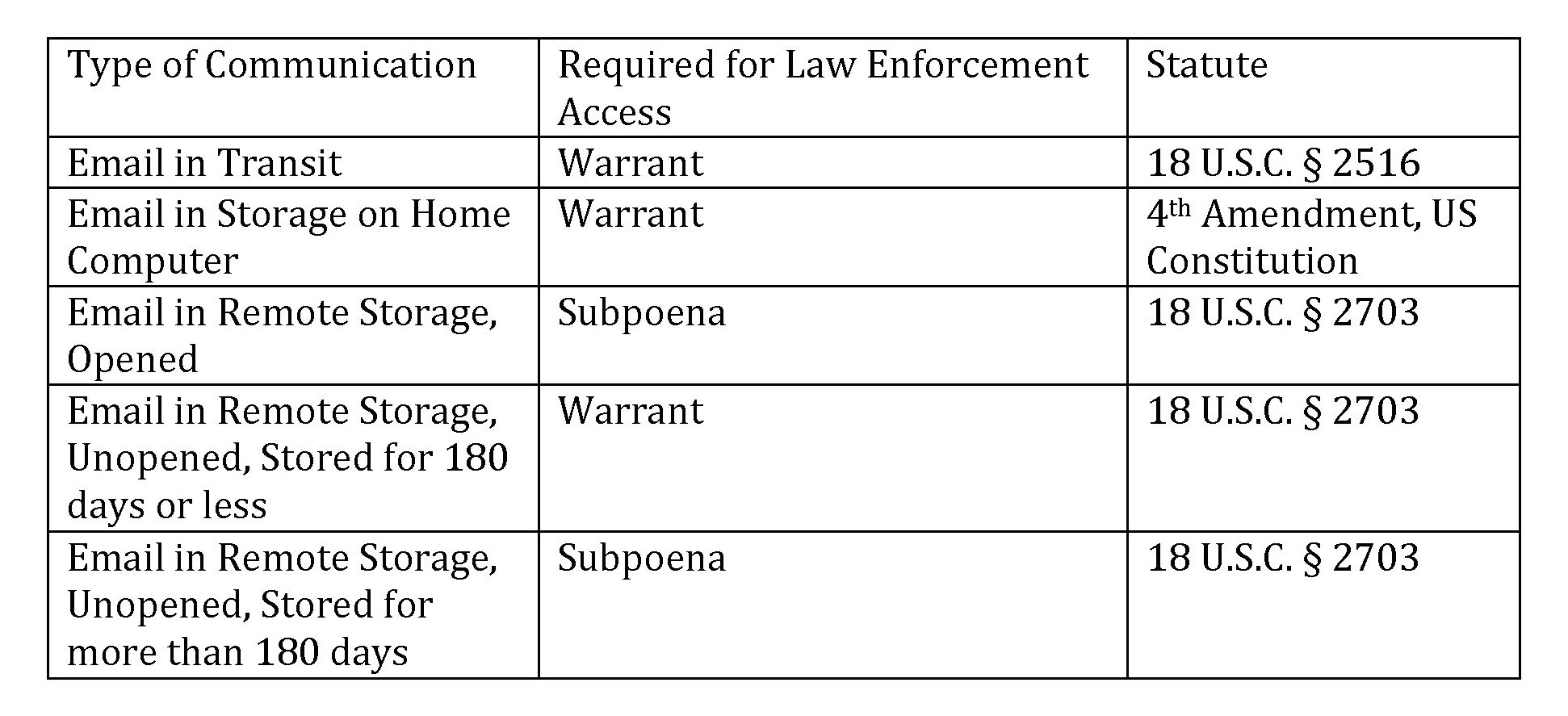
In addition to the specific government exceptions outlined above, there is other information that the government is empowered to collect from communications providers in the form of customer records. Under § 2703, an administrative subpoena, a National Security Letter ("NSL"), can be served on a company to compel it to disclose basic subscriber information. Section 2703 also allows a court to issue an order for records; whether an NSL or court order is warranted depends upon the information that is sought.
An NSL can be used to obtain the name; address; local and long distance telephone connection records, or records of session times and durations; length of service (including start date) and types of service utilized; telephone or instrument number or other subscriber number or identity, including any temporarily assigned network address; and means and source of payment for service (including any credit card or bank account number) of a subscriber. Although the breadth of information that can be gathered with an NSL is quite large, and was dramatically expanded with the USA PATRIOT Act, none of this information is supposed to include content.
All other non-content customer records have to be obtained by a court order under § 2703(d). These include transactional records such as "addresses of web sites visited by the customer and e-mail addresses of other individuals with whom the account holder has corresponded." Although an order for these materials is issued by a court, the court is not issuing a warrant based upon probable cause. Instead, § 2703(d) requires only that there be "specific and particularly facts showing that there are reasonable grounds to believe" that the records requested are "relevant and material to an ongoing criminal investigation."
As was stated, ECPA itself does not prohibit the disclosure of customer records to third parties. When the third party is the government, ECPA expressly permits the service provider to share customer records "if the provider reasonably believes than an emergency involving immediate danger of death or serious physical injury to any person justifies disclosure of the information." This authorization is found in § 2702 and was added as part of the USA PATRIOT Act. In practice, it allows law enforcement to forgo even the minimal burden of a subpoena or a court order and claim there is an emergency that necessitates the records being turned over. Although it is voluntary for the provider to act under this provision, many do in practice.
Fourth Amendment and Electronic Communications
The Fourth Amendment provides that:
The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.”
The Supreme Court has made clear that “[w]here a search is undertaken by law enforcement officials to discover evidence of criminal wrongdoing, . . . reasonableness generally requires the obtaining of a judicial warrant.” The fundamental purpose of the Fourth Amendment “is to safeguard the privacy and security of individuals against arbitrary invasions by government officials.” But not all government actions trigger scrutiny; “the Fourth Amendment's protections hinge on the occurrence of a ‘search,’ a legal term of art whose history is riddled with complexity.” A “search” occurs when the government infringes upon “an expectation of privacy that society is prepared to consider reasonable.” This standard breaks down into two discrete inquiries: “first, has the [target of the investigation] manifested a subjective expectation of privacy in the object of the challenged search? Second, is society willing to recognize that expectation as reasonable?”
Though the Supreme Court has never considered directly whether stored electronic communications are entitled to Fourth Amendment protection, the Court has assumed (without concluding) that individuals have a reasonable expectation of privacy in stored messages. Quon v. City of Ontario, CA, 560 U.S. 746, 748 (2010). The Court has also found that individuals have a legitimate expectation of privacy in their private communications. Nixon v. Administrator of General Services, 433 U.S. 425, 463 (1977). Several federal appellate courts have considered directly whether e-mails and other electronic messages are protected by the Fourth Amendment. The U.S. Court of Appeals for the Sixth Circuit held in 2010 that users have a reasonable expectation of privacy in e-mails stored by their internet service provider. United States v. Warshack, 632 F.3d 266 (6th Cir. 2010). This principle is now widely accepted, and even the Department of Justice has agreed that there is no principle basis to exclude certain types of e-mails from the warrant protections granted under the SCA. However, some courts have held that the to/from addresses of e-mail messages, the IP addresses of websites visited, and the total amount of data transferred to or from an account are not protected by the Fourth Amendment. United States v. Forrester, 495 F.3d 1041 (9th Cir. 2007).
Prior to the enactment of ECPA, the Supreme Court overturned a state law in New York that authorized the collection of private communications without sufficient particularity. Berger v. New York, 388 U.S. 41, 55 (1967). The Court noted that “The need for particularity and evidence of reliability in the showing required when judicial authorization of a search is sought is especially great in the case of eavesdropping. By its very nature eavesdropping involves an intrusion on privacy that is broad in scope.” Due to the intrusive nature of eavesdropping, the Court found that government eavesdropping on private communications would require “(1) prior judicial authorization, (2) specification of particular offenses said to justify the intrusion, (3) specification ‘with particularity’ of the conversations sought to be seized, (4) minimization of the duration of the wiretap, (5) termination once the conversation sought is seized, and (6) a showing of exigent circumstances justifying use of the wiretap procedure.” Nixon v. Administrator of General Services, 433 U.S. 425, 463 (1977). Congress incorporated these Berger-derived requirements into the Wiretap Act.
More recently, courts have begun to address the need for particularity and minimization in searches of e-mails and other electronic records. Judge Alex Kozinski outlined in United States v. Comprehensive Drug Testing, 621 F.3d 1162, 1180 (9th Cir.) (Kozinski, J., concurring), specific data minimization guidelines that have since been embraced by other courts. The CDT guidelines are:
- Magistrates should insist that the government waive reliance upon the plain view doctrine in digital evidence cases.
- Segregation and redaction must be either done by specialized personnel or an independent third party. If the segregation is to be done by government computer personnel, it must agree in the warrant application that the computer personnel will not disclose to the investigators any information other than that which is the target of the warrant.
- Warrants and subpoenas must disclose the actual risks of destruction of information as well as prior efforts to seize that information in other judicial fora.
- The government’s search protocol must be designed to uncover only the information for which it has probable cause, and only that information may be examined by the case agents.
- The government must destroy or, if the recipient may lawfully possess it, return non-responsive data, keeping the issuing magistrate informed about when it has done so and what it has kept.
Courts have also begun to address the issue of notification and warrant returns for e-mail searches. The Supreme Court has made clear since Berger that the government must provide notice of a search and an inventory of the return in order to satisfy the Fourth Amendment. United States v. Donovan, 429 U.S. 413, 429 n.19 (1977). However, some lower courts have interpreted ECPA’s notice requirement as being satisfied when the government notifies service providers, not individual users. The Government also frequently applies for gag orders in connection with ECPA orders to prevent service providers from notifying their users themselves. On April 14, 2016, Microsoft filed a lawsuit challenging the Department of Justice for orders which prevent the company from notifying users about the government’s e-mail search.
Reform Proposals
ECPA embodies many important and useful protections, but much has changed since ECPA was passed in 1986; from personal computing to the Internet and now the ubiquity of mobile devices, much of today's technology (and even much of yesterday's) was not conceived when the law was first drafted. ECPA has been amended several times, but has not been significantly modified since becoming law.
ECPA regulates when electronic communications can be intercepted, monitored, or reviewed by third parties, making it a crime to intercept or procure electronic communications unless otherwise provided for under law or an exception to ECPA. ECPA defines "electronic communication" as "any transfer of signs, signals, writing, images, sounds, data, or intelligence of any nature transmitted in whole or in part by a wire, radio, electromagnetic, photoelectronic or photooptical system that affects interstate or foreign commerce." This definition focuses on the transfer of the data - the time during which the packets of data are traveling between one point and the other. This creates and "on the wire" versus "off the wire" distinction that is becoming more difficult as technology advances.
Courts are in disagreement over the scope of ECPA’s e-mail protections in part due to the sharp distinctions drawn between stored communications and those in transit. What was once a clear distinction between interception of communications in transit vs. collection of stored messages in the telephone context is now increasingly muddled with e-mail. For example, the packets that make-up a single e-mail are broken apart, sent across multiple servers and routers, and then recombined and stored on remote computers to be made accessible to a user. It is unclear how ECPA applies at each of these stages: is an email considered in transit, and therefore governed by Title I, or is the message n "electronic storage" and governed by Title II. Title I, the Wiretap Act, and Title II, the Stored Communications Act, trigger different legal standards, which creates uncertainty for users, providers, law enforcement officers, and judges.
The adoption of cloud computing, while offering many benefits (such as convenience and ease of access), makes the need for ECPA reform more urgent. Whereas an e-mail stored on a home computer would be fully protected by the Fourth Amendment warrant requirement, only the Sixth Circuit has ruled that all e-mail stored on a remote, cloud computing server is protected. More and more information, including documents, e-mails, pictures, personal calendars, and locational data is being stored in the cloud. Much of this data has little or no protection under current law. Protections for locational data, in particular, have been widely discussed, but, to date, have not been added.
The 180 day rule within ECPA is also the subject of much criticism. When ECPA was passed in 1986, web-based e-mail, such as Gmail, did not exist. Instead, e-mail primarily existed in local intranets where clients would download their messages from the server and the server would, generally, not keep a backup. Congress presumed that any e-mails left on the server for more than 180 days should be treated like abandoned property. This distinction, however, is no longer as relevant today when customers have access to nearly unlimited cloud storage.
Congress has held several hearings on reforming ECPA, with technology companies and digital rights groups lobbying for clear standards that are adaptable to technological advances. Law enforcement has questioned the need to ECPA reform, fearing that reforms could decrease their ability to acquire digital information in a timely manner.
EPIC has advocated for a number of changes to ECPA including an across-the-board warrant requirement, search notice and returns for users, protection of location data, and mandatory data minimization and end-to-end encryption for commercial e-mail services.
Current Proposals
- Email Privacy Act of 2016
- Emergency Authorization Provision:
- Electronic Communications Transactional Records (“ECTR fix”)
- Sen. Patrick Leahy & Sen. Mike Lee, Electronic Communications Privacy Act Amendments Act of 2015, S. 356; Rep. Matt Salmon, H.R. 283
- Sen. Ron Wyden, GPS Act, S. 237; Rep. Jason Chaffetz,
- One Page Analysis
- Statement of Sen. Wyden
- Statement of Rep. Chaffetz
- Statement of Rep. DelBene
- Rep. Kevin Yonder, Email Privacy Act, H.R. 699
- The Email Privacy Act, House Judiciary Committee, December 1, 2015.
- The Electronic Communications Privacy Act (ECPA), Part 2: Geolocation Privacy and Surveillance, House Judiciary Committee, Subcommittee on Crime, Terrorism, Homeland Security and Investigations, April 25, 2013.
- The Electronic Communications Privacy Act (ECPA), Part 1: Lawful Access to Stored Content, House Judiciary Committee, Subcommittee on Crime, Terrorism, Homeland Security and Investigations, March 19, 2013.
- The Electronic Communications Privacy Act: Government Perspectives on Protecting Privacy in the Digital Age, Senate Judiciary Committee, April 6, 2011.
- ECPA Reform and the Revolution in Cloud Computing, House Judiciary Committee, September 23, 2010.
- "The Electronic Communications Privacy Act: Promoting Security and Protecting Privacy in the Digital Age," Senate Judiciary Committee, September 22, 2010.
- ECPA Reform and the Revolution in Location Based Technologies and Services, House Judiciary Committee, June 24, 2010.
- Electronic Communications Privacy Act Reform, House Judiciary Committee, May 5, 2010.
- Office of Legal Education Executive Office for United States Attorneys, Searching and Seizing Computers and Obtaining Electronic Evidence in Criminal Investigations, Department of Justice (2009).
- Mary Jo White, Letter to Senate Judiciary Committee, Securities and Exchange Commission, April 24, 2013
- SEC Investigations Manual Chapter 12 (Revised), SEC/OIG Office of Investigations (July 31, 2015)
- Kristina Irion, Accountability unchained: Bulk Data Retention, Preemptive Surveillance, and Transatlantic Data Protection in: Visions of Privacy in a Modern Age (M. Rotenberg, J. Horwitz, and J. Scott, eds. 2015)
- Laura K. Donohue, Section 702 and the Collection of International Telephone and Internet Content, 38 Harv. J.L. & Pub. Pol'y 117 (2015)
- Andrew Bagley, Don't Be Evil: The Fourth Amendment in the Age of Google, National Security, and Digital Papers and Effects, 21 Albany Law Journal of Science and Technology 153 (2011).
- Nathan Henderson, The Patriot Act's Impact on the Government's Ability to Conduct Electronic Surveillance of Ongoing Domestic Communications, 52 Duke L.J. 179 (2002).
- Ilana Kattan, Cloudy Privacy Protections: Why the Stored Communications Act Fails to Protect the Privacy of Communications Stored in the Cloud, 13 Vanderbilt Journal of Entertainment and Technology Law 617 (2011).
- Haley Plourde-Cole, Back to Katz: Reasonable Expectation of Privacy in the Facebook Age, 38 Fordham Urban Law Journal 571 (2010).
- The Electronic Communications Privacy Act of 1986 (ECPA), Pub. L. 99-508, Oct. 21, 1986, 100 Stat. 1848 (1986).
- Wire and Electronic Communications Interception and Interception of Oral Communications, 18 U.S.C. Chapter 119.
- Stored Wire and Electronic Communications and Transactional Records Access, 18 U.S.C. Chapter 121.
- Pen Registers and Trap and Trace Devices, 18 U.S.C. Chapter 206.
- California Electronic Communications Privacy Act, Senate Bill No. 178, Chapter 651
- Katz v. United States, 389 U.S. 347 (1967).
- Smith v. Maryland, 442 U.S. 735 (1979).
Rep. Yoder. Kevin introduced the Email Privacy Act in February 2015. The initial proposal includes an extension of the warrant requirement to communications stored for more than 180 days and a requirement of notice before email searchers. The proposed amendment passed House in April 2016 (419-0), but the notice requirement was left out. Currently, the ECPA reform bill is pending in front of the Senate.
Sen. Jeff Sessions proposed an emergency disclosure rule to the Act which would give an exception to the warrant requirements in times of claimed emergency. Under the current act, companies are allowed to voluntarily make emergency disclosures to the government, but the amendment would make such disclosures mandatory.
Sen. Lindsey Graham proposed a “fix” to ECPA which would grant the FBI access to browsing history and location information with National Security Letter (“NSL”). These letters are issued directly by local FBI offices without any court approval or supervision. Besides, most NSLs contains a gag order which can prevent the receiver of such letter from disclosing the government’s request.
State Laws
California Electronic Communications Privacy Act
The California Electronic Communications Privacy Act was approved by the Governor on October 8, 2015. The CalECPA covers a broader range of issues than ECPA and offers protection over all electronic communication information.
Under the CalECPA, the government must obtain a search warrant or subpoena before accessing “any information about an electronic communication or the use of an electronic communication service, including, but not limited to, the contents, sender, recipients, format, or location of the sender or recipients at any point during the communication, the time or date the communication was created, sent, or received, or any information pertaining to any individual or device participating in the communication, including, but not limited to, an IP address.” In particular, CalECPA specifically covers location data, while the federal ECPA does not explicitly require a warrant for accessing such data.
In addition, the CalECPA also prohibits the government from obtaining electronic communication information through physically accessing individual’s electronic device. The federal ECPA does not specify any requirements about device-stored data.
Additional Resources
Congressional Hearings
Government Reports
Internet Company Procedures
Model Gag Applications & Orders
Law Reviews
Legal Resources
Websites
Latest News
- Jennifer Daskal, Beware of the Emergency Exception Loophole in the Email Privacy Act, Just Security (June 7, 2016)
- Ellen Nakashima, FBI Wants Access to Internet Browser History without a Warrant in Terrorism and Spy Cases, Wash. Post (June 6, 2016)
- Robyn Greene, FBI’s Push to “Fix a Typo” Would Really Expand Its Surveillance Authority, Just Security (Feb 17, 2016)
- Mario Trujillo, California Puts Email Privacy Law on the Books, The Hill (Oct 09, 2015)
- Mario Trujillo and David McCabe, Overnight Tech: Senate Gets Late Start on Email Privacy The Hill (Sept. 15, 2015)
- Sen. Patrick Leahy & Sen. Mike Lee, Update Privacy Laws for the Digital Age, Real Clear Policy (Jan. 28, 2015)
- Cyrus Farivar, Unprecedented E-mail Privacy Bill Sent to Texas Governor's Desk, ArsTechnica (May 28, 2013).
- Editorial, Upgrade Protections of Digital Records, Seattle Times, May 16, 2013
- Patrick McGreevy, California Senate Backs Requiring Warrants When Police Want E-mails, L.A. Times, May 13, 2013
Share this page:
Subscribe to the EPIC Alert
The EPIC Alert is a biweekly newsletter highlighting emerging privacy issues.







